Levelling Up ZAP with OAST
This post is a part of a series of posts related to my Google Summer of Code ‘21 project.
A little background for readers unfamiliar with ZAP or OAST:
What is ZAP?
Zed Attack Proxy (ZAP) is a fully open-source web application penetration testing suite. It is an OWASP flagship project and is widely used by developers and bug bounty hunters alike. It offers excellent Dynamic Application Security Testing (DAST) functionalities and there are several ways to automate and integrate it in your workflow. Find out more about ZAP at zaproxy.org.
What is OAST?
Out-of-band Application Security Testing (OAST) involves sending payloads that trick the target into connecting with a second computer that is also controlled by the attacker. This article by PortSwigger is a good read on the topic.
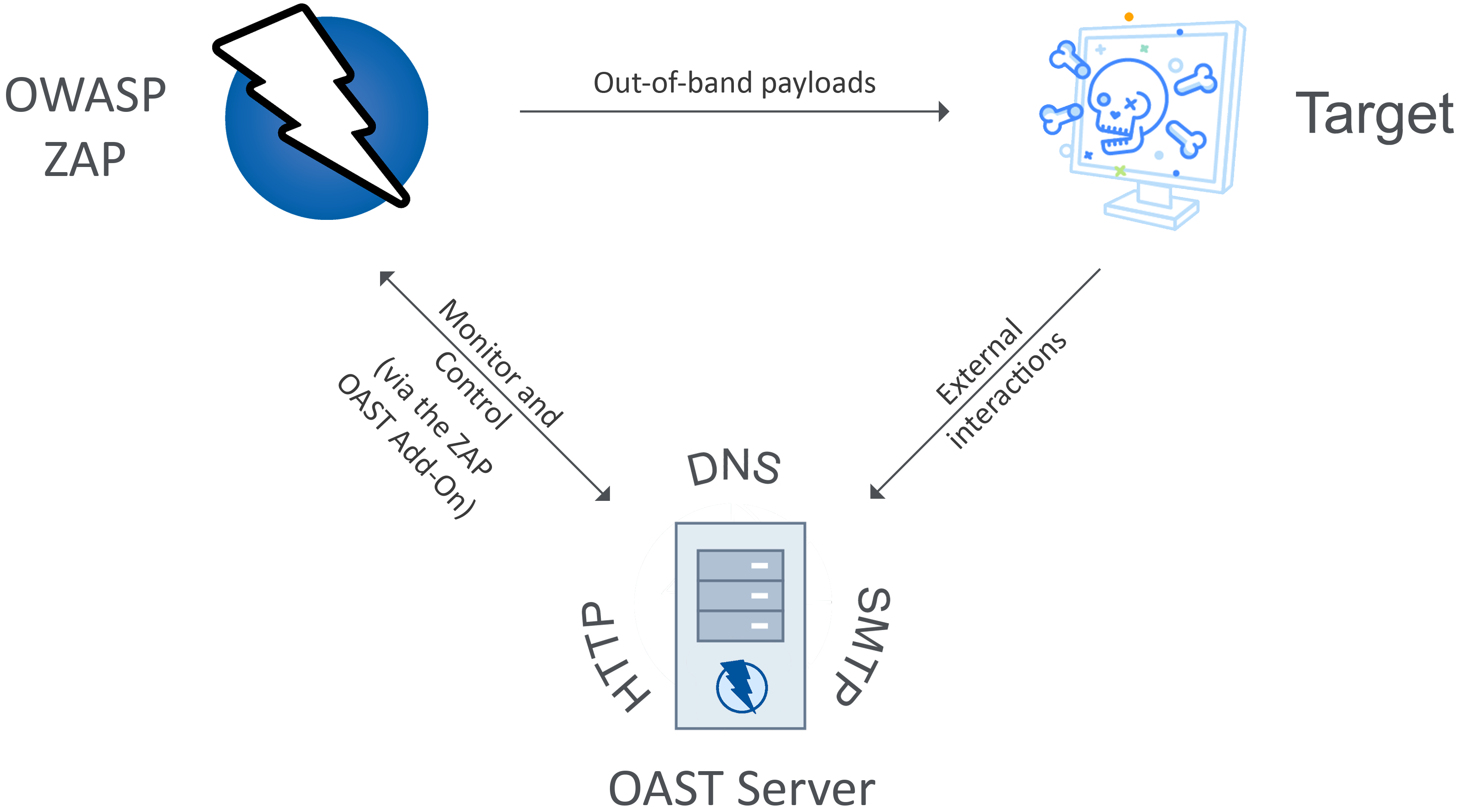
|
| ZAP and OAST |
The OAST add-on for ZAP
The OAST functionality for ZAP will be made available as a ZAP add-on.
The add-on will provide an interface in ZAP to connect to an OAST server, much like the existing Callback Functionality. The user is expected to host their own OAST server and provide connection details to ZAP.
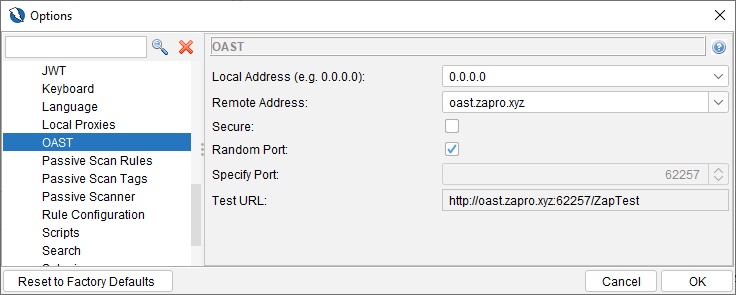
|
| ZAP OAST Options (Preview) |
Then, at an interval that can be set by the user, ZAP will poll the OAST server for any interactions that it received and display them in a separate tab in the bottom panel.
Note that the OAST server must serve responses in a format that ZAP is able to understand. This will be documented and available soon. This add-on is going to be written in a way that will allow you to use any service with it. I’m going to be using BOAST to test and develop the add-on.
The OAST add-on will also be configurable via the ZAP Automation Framework, API and the CLI.
Attack Vectors
The OAST add-on will be bundled with many active scan rules that will make use of the service if enabled. These scan rules haven’t been decided yet, but many existing scan rules will be updated and new ones will be introduced.
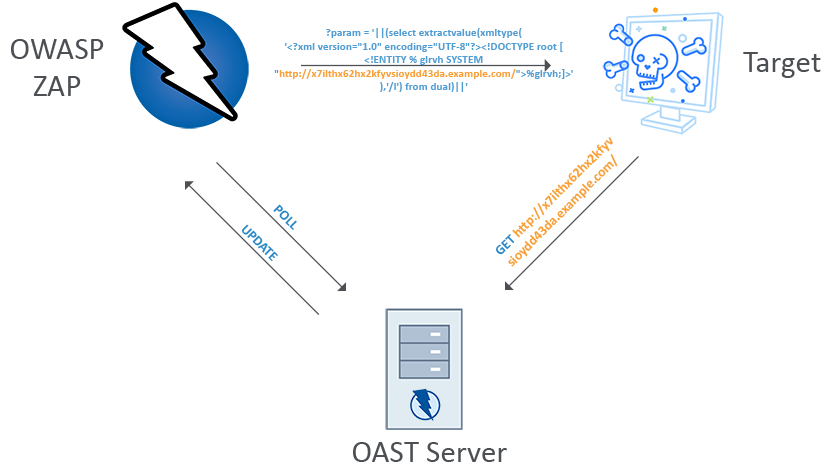
|
| An example of Blind SQLi with ZAP and OAST |
How can I get the add-on?
The add-on is still in development and will be available soon in the ZAP Marketplace :). For more updates keep an eye on the ZAP developer group or the ZAP GitHub repositories.
Further information
You can find my proposal here for more information about the implementation of the OAST add-on. All feedback / comments / requests for features appreciated!
I am very excited about this project and will be sharing more soon! ✨